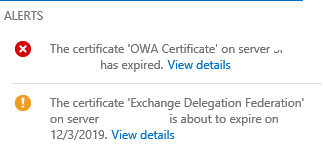
Exchange Delegation Federation / Microsoft Federation Gateway / Renew Certificate
From Ilianko
EAC is alerting for certificate expiration.
Renew before the certificate before expiration.
Contents
Generate new self signed certificate from exchange shell
Key Identifier ( Random name for the key)
$:\> $SKI = [System.Guid]::NewGuid().ToString("N");
$:\> echo $SKI
3ecaf8d9942c4fb4848e6201810e0734
Create Key
New-ExchangeCertificate -DomainName 'Federation' -FriendlyName "Exchange Delegation Federation" ` -Services Federation -SubjectKeyIdentifier $SKI -PrivateKeyExportable $true
Thumbprint Subject ---------- ------- 133F83817AD86C127C0A71B92214C52D6B3A4D31 CN=Federation
Set the "next" in exchange
$:\>Set-FederationTrust -Identity "Microsoft Federation Gateway" -Thumbprint 133F83817AD86C127C0A71B92214C52D6B3A4D31 -RefreshMetaData
WARNING: The federation trust has changed to prepare for the usage of a new certificate for Federation. ` You should update all TXT proof-of-ownership records that were previously set in DNS for all the domains ` configured for Federation before publishing the new certificate. The new hash-value should be replaced with the OrgNextCertificate proof value output generated with ` "Get-FederatedDomainProof -DomainName example.com".
Update DNS TXT record
Find and update the TXT record responsible for Federation
$:\>nslookup -type=txt example.com 8.8.8.8
example.com text = "v=spf1 mx -all" example.com text = "google-site-verification=... example.com text = "qwa3SWMSP+278DT56LL2y+QmQ33UgQzRuofsRjLrZIyhl8O...=="
Authoritative answers can be found from:
Get-FederatedDomainProof -DomainName example.com| Format-List Thumbprint,Proof
//new Thumbprint : 133F83817AD86C127C0A71B92214C52D6B3A4D31 Proof : asaq33FMhbo05dK8M+Tek1gj7frqmnatO1hM5MWLx98yLivsrIJQ6M1Zk4W90bmSE4...==
//old Thumbprint : 993FF8C8E1F312FE59CF6C047C60FAF35AC33F66 Proof : qwa3SWMSP+278DT56LL2y+QmQ33UgQzRuofsRjLrZIyhl8O...==
New TXT record
$:\>nslookup -type=txt example.com 8.8.8.8
example.com text = "v=spf1 mx -all" example.com text = "google-site-verification=... example.com text = "asaq33FMhbo05dK8M+Tek1gj7frqmnatO1hM5MWLx98yLivsrIJQ6M1Zk4W90bmSE4...=="
New TXT record
$:\>nslookup -type=txt example.com ns.local.dns
example.com text = "v=spf1 mx -all" example.com text = "google-site-verification=... example.com text = "asaq33FMhbo05dK8M+Tek1gj7frqmnatO1hM5MWLx98yLivsrIJQ6M1Zk4W90bmSE4...=="
Test before change
$:\> Test-FederationTrust -UserIdentity mail@example.com
Begin process.
STEP 1 of 6: Getting ADUser information for mail@example.com...
RESULT: Success.
STEP 2 of 6: Getting FederationTrust object for mail@example.com...
RESULT: Success.
STEP 3 of 6: Validating that the FederationTrust has the same STS certificates as the actual certificates published by the STS in the federation metadata.
RESULT: Success.
STEP 4 of 6: Getting STS and Organization certificates from the federation trust object...
RESULT: Success.
Validating current configuration for KLJWLKJDWL57623.example.com...
Validation successful.
STEP 5 of 6: Requesting delegation token...
RESULT: Success. Token retrieved.
STEP 6 of 6: Validating delegation token...
RESULT: Success.
Closing Test-FederationTrust...
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : FederationTrustConfiguration
Type : Success
Message : FederationTrust object in ActiveDirectory is valid.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : FederationMetadata
Type : Success
Message : The federation trust contains the same certificates published by the security token service in its federation metadata.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : StsCertificate
Type : Success
Message : Valid certificate referenced by property TokenIssuerCertificate in the FederationTrust object.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : StsPreviousCertificate
Type : Success
Message : Valid certificate referenced by property TokenIssuerPrevCertificate in the FederationTrust object.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : OrganizationCertificate
Type : Success
Message : Valid certificate referenced by property OrgPrivCertificate in the FederationTrust object.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : TokenRequest
Type : Success
Message : Request for delegation token succeeded.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
Id : TokenValidation
Type : Success
Message : Requested delegation token is valid.
Apply the "Next" certificate
Set-FederationTrust -Identity "Microsoft Federation Gateway" -PublishFederationCertificate
Errors
FederationTrust object is expired
Certificate was created with local time. This was 2 hours earlier ...
Solution: wait https://jesperstahle.azurewebsites.net/?p=142
Error:
... STEP 4 of 6: Getting STS and Organization certificates from the federation trust object... WARNING: Could not retrieve orgPrivCertificate from GetOrganizationCertificates
Closing Test-FederationTrust... ... RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78 Id : OrganizationCertificate Type : Error Message : Certificate referenced by property OrgPrivCertificate in the FederationTrust object is expired. Error: GetOrganizationCertificates(federationTrust) returned null when called in Process() + CategoryInfo : NotSpecified: (:) [], LocalizedException + FullyQualifiedErrorId : [Server=mail,RequestId=3fa41912-ddfa-41af-b063-92cb4fa6623d,TimeStamp=12/2/2019 8:46:58 AM] [FailureCategory=Cmdlet- LocalizedException] 3CE8F0B2 + PSComputerName : mail.example.com
Certificate
$:\> get-federationtrust |select *
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78
ApplicationIdentifier : 0000000048307
ApplicationUri : KLJWLKJDWL57623.example.com
OrgCertificate : [Subject]
CN=Federation
[Issuer]
CN=Federation
[Serial Number]
JHKJD6756JHG26KJ54D6WD46QW
[Not Before]
12/2/2019 9:23:23 AM
[Not After]
12/2/2024 9:23:23 AM
Deleted Old Certificate
The old certificate is not automatically removed. After remove with mmc console the following error appears.
RunspaceId : ea565-64c3-4656-9e7f-420a7b4a4d78 Id : OrganizationPreviousCertificate Type : Error Message : Unable to find the certificate referenced by property OrgPrevPrivCertificate in the FederationTrust object.
WARNING: An unexpected error has occurred and a Watson dump is being generated: Object reference not set to an instance of an object. Object reference not set to an instance of an object. + CategoryInfo : NotSpecified: (:) [Test-FederationTrust], NullReferenceException + FullyQualifiedErrorId : System.NullReferenceException,Microsoft.Exchange.Management.SystemConfigurationTasks.TestFederationTrust + PSComputerName : mail.example.com
Solution: Clear the OrgPrevPrivCertificate with ADSIEdit
- Locate CN=Configuration, DC=<DOMAIN>, DC=<COM>, CN=Services , CN=Microsoft Exchange, CN=<ORGANIZAION NAME>, CN=Federation Trusts.
- Right-click CN=Microsoft Federation Gateway, and then click Properties.
- Double-click the msExchFedOrgNextCertificate property, and clear the value.
Links